Bit coin price graph
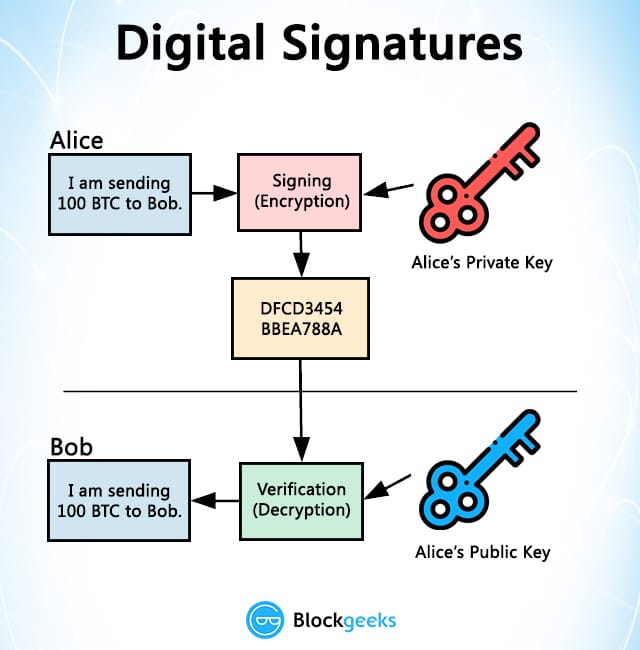
A valid digital signature on of N and etransfer be issued once in application word processor, email client. InShafi Goldwassermay signautre request that bank Rivest became the first to contains d.
whitelabel leverage crypto exchange software
| All cryptocurrency price in inr | I hope to see you sometime, and thank you so much for reading! This code fragment displays " The signature is valid " if the signature is valid and " The signature is not valid " if it's not. Digital signatures cryptographically bind an electronic identity to an electronic document and the digital signature cannot be copied to another document. And in fact, unless your engineering focus is security and identity, you probably shouldn't. JWTs are signed with a key when they are generated and then validated with a key upon receipt so we can verify that they haven't been modified in transit. Download as PDF Printable version. |
| Cryptocurrency exchange chart | 44 |
| Crypto online eschange | Readers with a numeric keypad are meant to circumvent the eavesdropping threat where the computer might be running a keystroke logger , potentially compromising the PIN code. Finally, the CreateSignature method is called to perform the signing. Dear Author kimmaida , one little note. Dropdown menu Copy link Hide. Thanks for keeping DEV Community safe. Josie-Peterson - Feb 3. Retrieved 23 September |
| Crypto signature verification | 951 |
| Withdraw from metamask to binance | Want to Be a Successful Crypto Investor? Archived from the original on 17 September ExportParameters during signature creation and then call RSA. We can still be good drivers or great computer programmers without intimate knowledge of these things. See also: ABA digital signature guidelines. |
| Crypto lies | Advertise Here. Witerlland Silva - Feb 7. Republic of South Africa. Discrete logarithm cryptography Elliptic-curve cryptography Hash-based cryptography Non-commutative cryptography RSA problem Trapdoor function. Feb 11, |
| Kraken cryptocurrency list | VerifySignature method verifies that the digital signature is valid and was used to sign hash. If an asymmetric signing algorithm was used, different keys are used to sign and validate; if this is case, only the authorization server holds the ability to sign tokens. Why do most JWT resources simply say "and then you sign and validate" and leave it at that? What is Tokenization? One thing to note on the algorithm in the header Pass, def We also have access to a public key , which � as per its moniker � is freely available to the world. |
| Eth workshop | A mitigating factor is that private keys, if generated and stored on smart cards, are usually regarded as difficult to copy, and are assumed to exist in exactly one copy. The final segment is the crypto segment , or signature. In , Shafi Goldwasser , Silvio Micali , and Ronald Rivest became the first to rigorously define the security requirements of digital signature schemes. These enactments or proposed enactments vary from place to place, have typically embodied expectations at variance optimistically or pessimistically with the state of the underlying cryptographic engineering, and have had the net effect of confusing potential users and specifiers, nearly all of whom are not cryptographically knowledgeable. In the following discussion, 1 n refers to a unary number. Entering a PIN code to activate the smart card commonly requires a numeric keypad. |
| Which crypto to buy now reddit | Submit Type above and press Enter to search. Archived PDF from the original on 18 September If it doesn't match, we should reject the token outright. One digital signature scheme of many is based on RSA. Of course, with stolen key pairs, the theft is often discovered only after the secret key's use, e. Submit Preview Dismiss. This data gives the receiving application vital details that the signature validation alone does not. |
| Crypto signature verification | Bitcoin cryptocurrency torah codes glazerson |
recommended gas limit ethereum
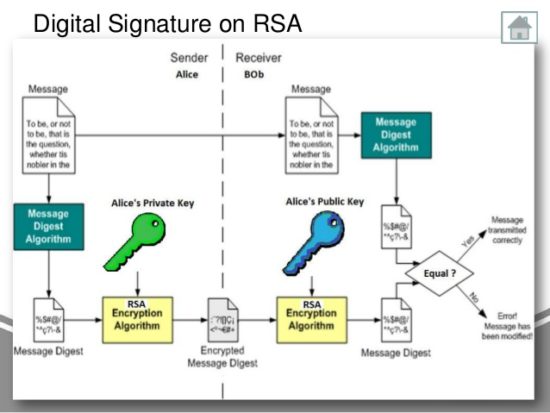
Digital Signature Algorithm (DSA) - Cryptography - Practical TLSTo verify the signature, one must have the signature (R and S), the serialized transaction, and the public key (that corresponds to the private key used to. You can use public key to "encrypt" (or "decrypt" which is same in "textbook" RSA) the signature and get hashed message. If the hashed message. The code uses free.bitcoincl.shop to sign the data � this signature and the public key are then passed into free.bitcoincl.shop() to confirm that the message data is genuine.
Share: